Game Description
Mission IHI is a unique game that challenges players to step into the shoes of both ethical hackers (Red Team) and cybersecurity defenders (Blue Team). As a Red Team player, your objective is to exploit vulnerabilities in a simulated system, uncovering its weaknesses. However, the true test lies in switching gears and becoming a Blue Team player. Here, you must leverage your newfound knowledge to patch the vulnerabilities you identified earlier, fortifying the system's defences. Through this immersive experience, players gain a comprehensive understanding of information security concepts, fostering critical thinking and problem-solving skills.
MISSION IHI
offers a fun and engaging way for children to learn about information security concepts, empowering them with the needed knowledge to consider a career in cybersecurity as they grow
About Us
Infosec4tc is an information security training and consultancy company established in 2016. We specialize in transforming information security training for various segments of students. Our focus includes non-technical students, young learners preparing for the information security market to increase their awareness, and professionals already working in information security who seek career advancement
CERTIFICATE

Once you finish this game, you'll not only level up your cybersecurity skills but also unlock an epic certificate of completion to showcase your achievement!
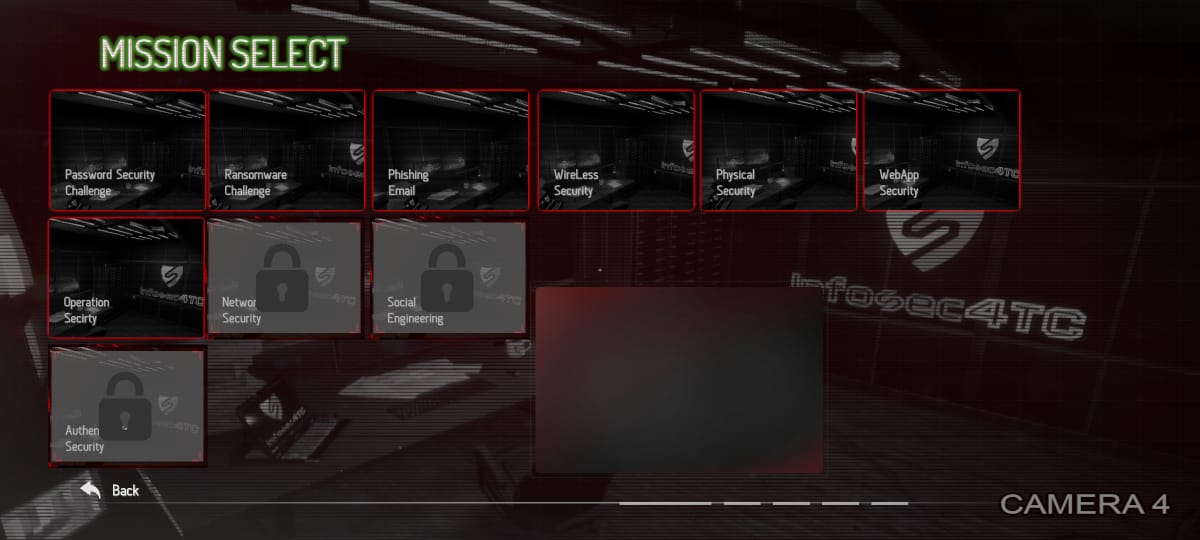
Missions Security Domains
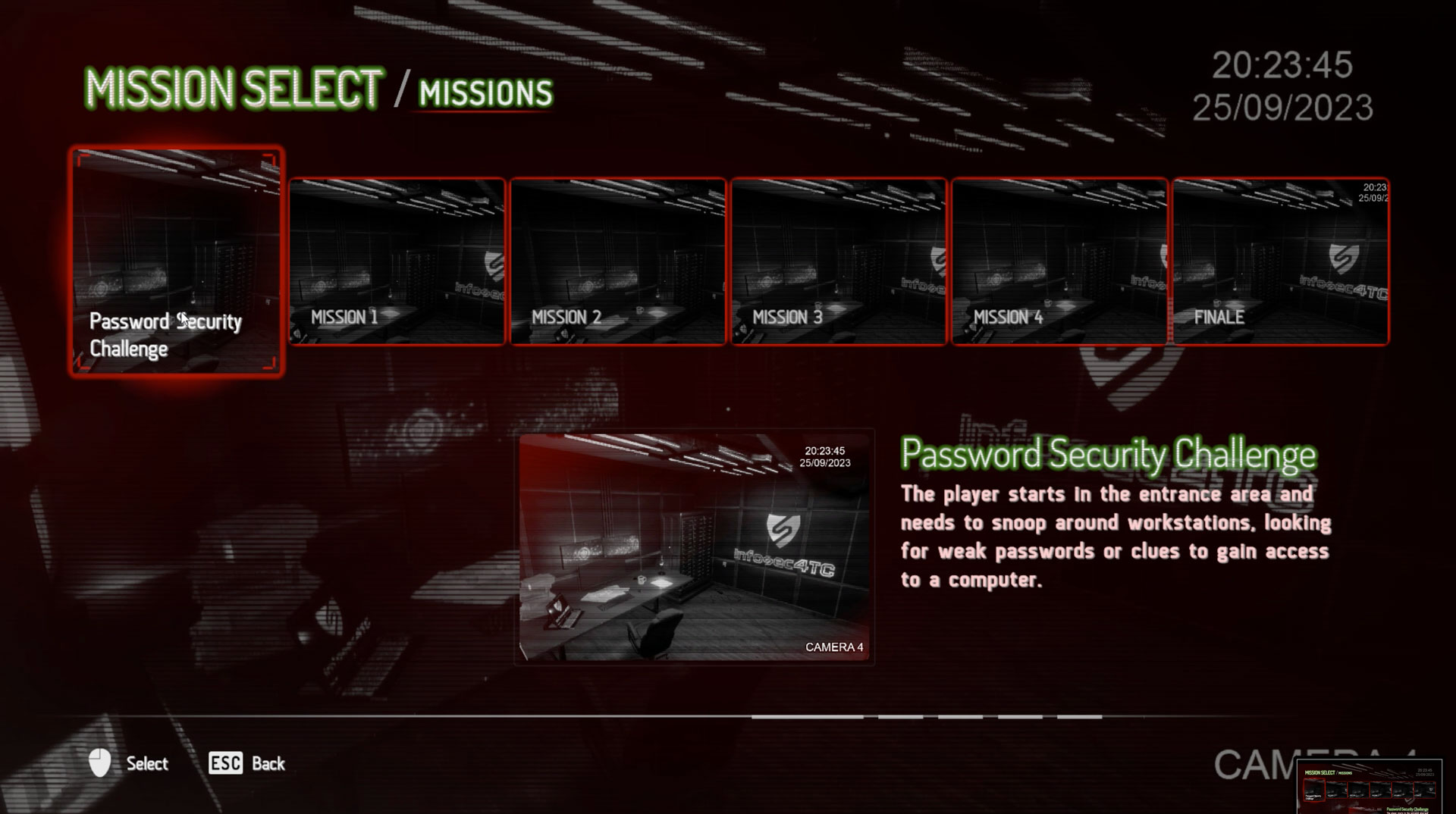
Password Security
your mission is simple guess the laptop password, hack into the system and replace it with a stronger password . Get ready to snoop, strategize, and outsmart security measures to achieve your goal! How long will it take you to crack the code and secure your success !
Ransomware Challenge
your mission is all about discovering how ransomware attacks exploit both technical weaknesses and human vulnerabilities. you will need to choose your targets wisely and then defend the systems against relentless assaults. Are you ready to face the challenge and see if you have what it takes to protect your virtual domain from future attacks?
Phishing e-mail
you are faced with threats sneaking beyond the physical world. you will encounter ticking time bombs waiting in your virtual mailbox. Can you harness the power of phishing emails to launch attacks, and then master the art of prevention to stop them in their tracks? Let’s see!
Wireless security
Equipped with gadgets of cutting-edge tools and gadgets to aid you in your mission to hack into and defend network connections. Will you demonstrate mastery over these tools and use them wisely to navigate the challenges ahead, hacking into networks and fortifying defenses with precision and skill?
Physical Security
the importance of safeguarding against physical threats becomes a must. As you navigate through the virtual landscape, remember that securing physical access is just as crucial as protecting digital data. Can you rise to the challenge and defend against potential breaches in this dynamic physical environment?
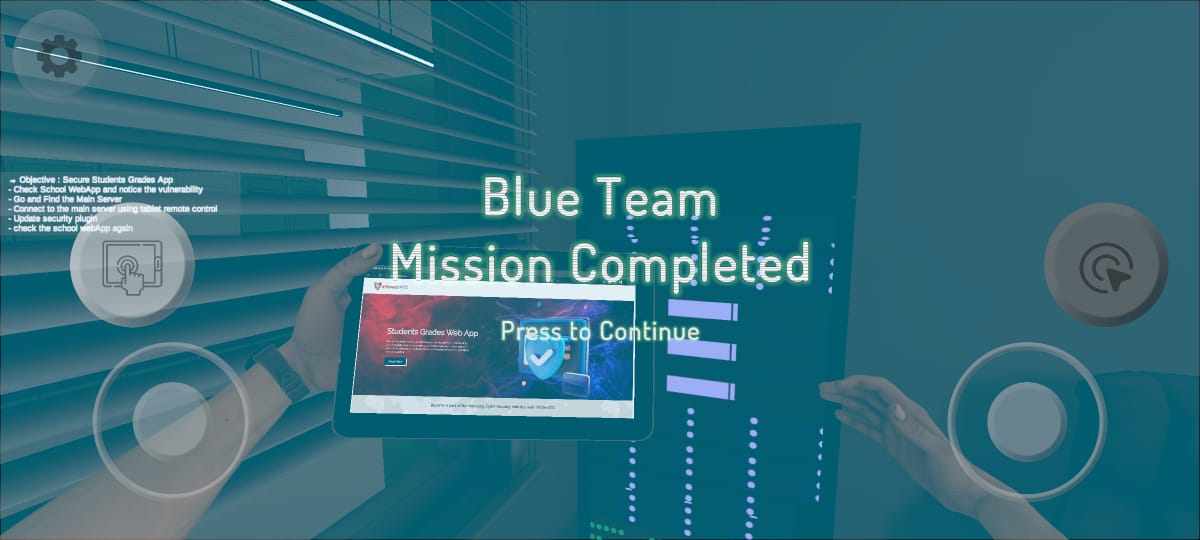
Webapp security
hacking into the secure database containing students' grades. As you get on on this daring mission, you'll uncover the vulnerabilities in the system and exploit them to access sensitive data. But beware, the clock is ticking, and you must act swiftly to avoid detection. Can you outsmart the system and manipulate grades, only to turn around and fortify the defences to prevent future breaches? It's a high-stakes game of cat and mouse, where every move counts!
Operations Security
Simplicity is deceptive. you must navigate the intricacies of gathering operational data and details without raising suspicion. Can you maintain a low profile and accomplish your mission without getting caught? Keep your wits about you as you delve into the heart of the operation!
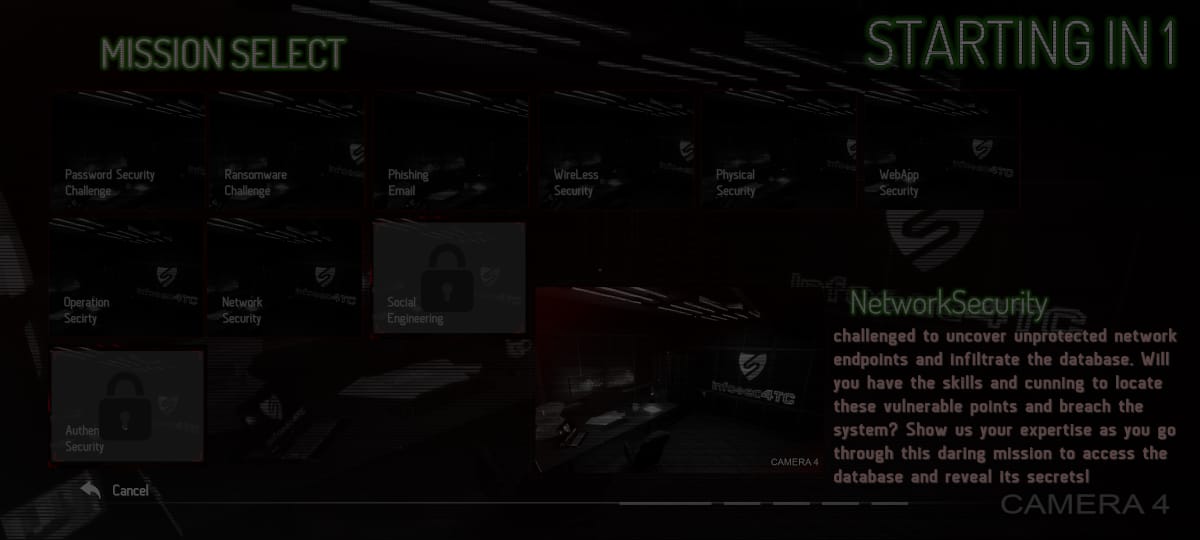
Network Security
challenged to uncover unprotected network endpoints and infiltrate the database. Will you have the skills and cunning to locate these vulnerable points and breach the system? Show us your expertise as you go through this daring mission to access the database and reveal its secrets!
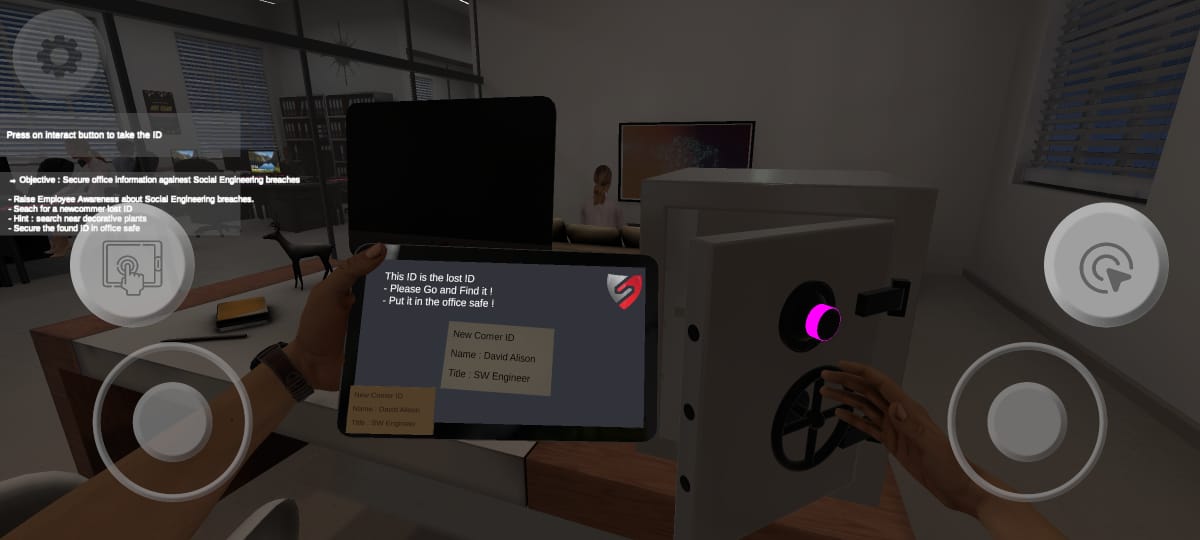
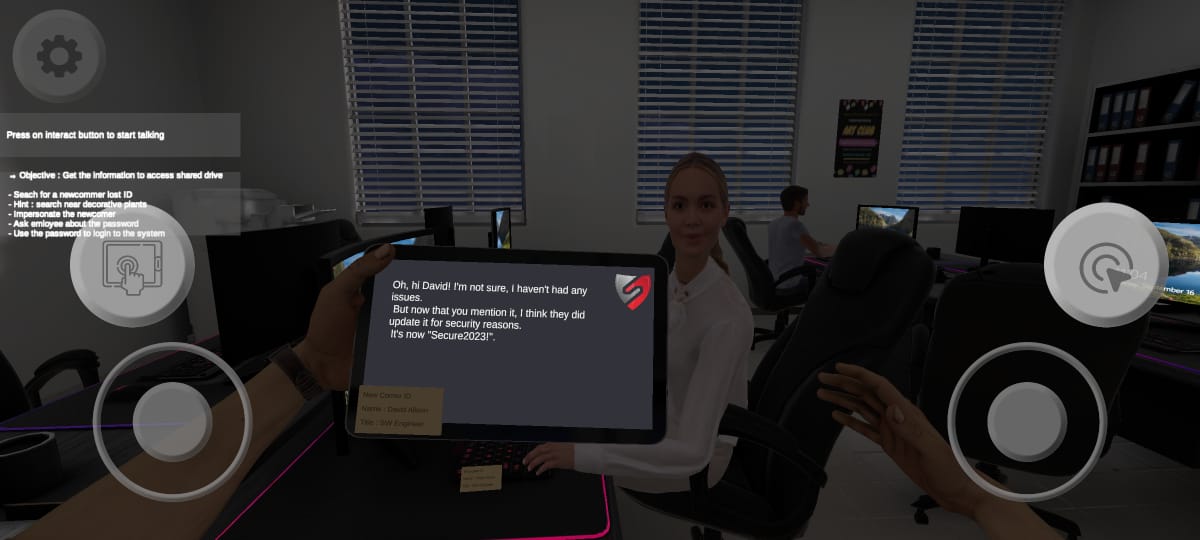
Social Engineering
The mission is to gather crucial information needed to access the shared drive. Prepare to navigate through virtual obstacles and outsmart security measures as you strive to obtain the necessary data. Can you overcome the challenges and secure access to the shared drive? The fate of your mission hangs in the balance!
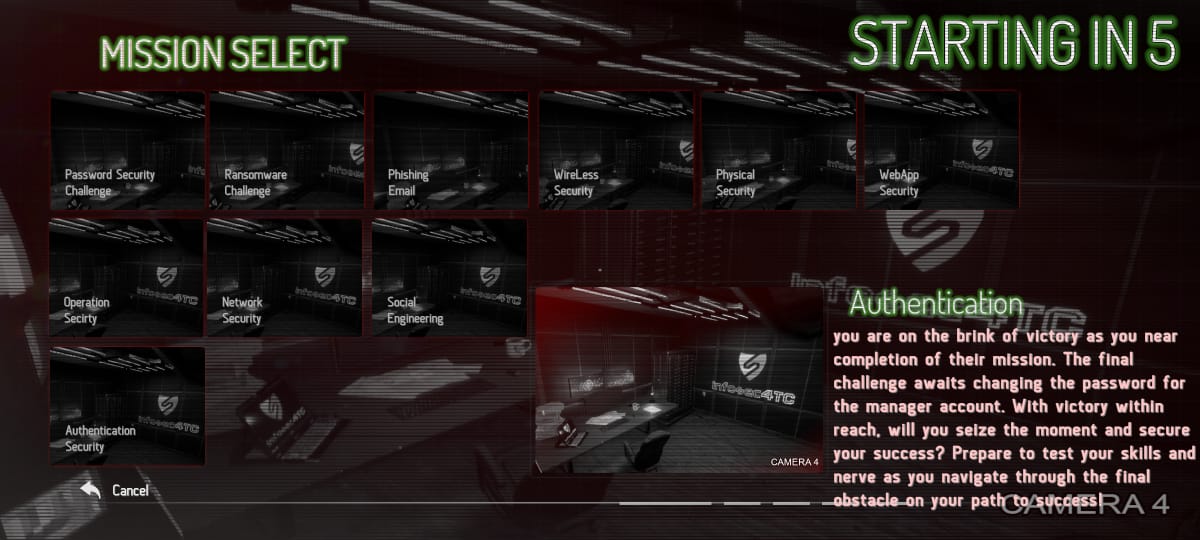
Authentication
you are on the brink of victory as you near completion of their mission. The final challenge awaits changing the password for the manager account. With victory within reach, will you seize the moment and secure your success? Prepare to test your skills and nerve as you navigate through the final obstacle on your path to success!
Why Mission IHI
Immersive Learning.
This game goes beyond traditional classroom lectures by placing students in the shoes of both ethical hackers and cybersecurity defenders. This hands-on approach fosters deeper understanding, critical thinking, and problem-solving skills.
Comprehensive Skill Development.
Mission IHI covers a wide range of cybersecurity concepts, from identifying vulnerabilities to implementing effective security measures. Students gain practical experience in areas like penetration testing, vulnerability assessment, and incident response.
Dual Role-Playing.
By switching between Red Team and Blue Team roles, students gain a holistic perspective on cybersecurity. They learn how attackers exploit vulnerabilities and how defenders can mitigate those risks, fostering a well-rounded understanding of the entire cyber defence ecosystem.
Scalability and Accessibility.
Mission IHI is available on various platforms, making it accessible to students with diverse learning styles and technological preferences. The game can be seamlessly integrated into existing curriculum or used as a standalone learning tool.
Fun and Engaging.
Learning doesn't have to be boring! Mission IHI incorporates gamification elements to keep students engaged and motivated. They can compete with peers, unlock achievements, and track their progress, making the learning process enjoyable and rewarding.
Cost-Effective Solution.
Compared to traditional cybersecurity training programs, Mission IHI offers a cost-effective and scalable solution to equip your students with essential cybersecurity skills.
Leaderboard
Compete with other players and climb the leaderboard by demonstrating your proficiency in both Red Team and Blue Team roles
Tutorials
Access comprehensive tutorials to learn about various cybersecurity concepts and hacking techniques
Challenges
Participate in time-bound challenges to test your skills under pressure and hone your reflexes
Community forum
Connect with other players, share experiences, and learn from each other.